Welcome to the discussion thread about this lecture section. Here you can feel free to discuss the topic at hand and ask questions.
hash’s all you need to know its one way!! no turning back…
Im very curious how to check hashes interface friendly in the end in different applications.
Just finished a section without any homework. Wohoo! I can go home early!! 
Just wanted to confirm my current understanding.
The public key is the sha256 of the private key and the wallet address is the RIPEMD160 of the public key?
Hey Ivan, I want to start similar curses in Lithuania and was thinking maybe you can help me?
Yeah I’m green on the hashing algorithms myself. I don’t quite get the “handshake” idea but I’m looking forward to when I have my head around it so to speak. Actually… I was just thinking it works like this.
Person A sends person B a public key.
B puts his private key with A’s public key and creates a hash.
B sends this hash to A.
A mixes this hash with his private key to produce another hash.
A sends this hash to B.
Both A and B now have unique private hashs that are used to decrypt each other’s messages… Right?
Hash is a cryptographfical timestamp/fingerprint between every block.
No way going back after that. It is final
Hash rate is something that is important with this type of technology.
Not according to this link:
https://en.bitcoin.it/wiki/Technical_background_of_version_1_Bitcoin_addresses
Half way down the page, there’s a list of the different conversion stages in the section How to create Bitcoin Address
It seems that both SHA-256 and RIPEMD-160 are used to convert the public key into a Bitcoin address. There are also some other stages, and SHA-256 is actually used multiple times.
Probably not the straightforward answer you hoped for, but I hope that helps! 
Hi Ivan,
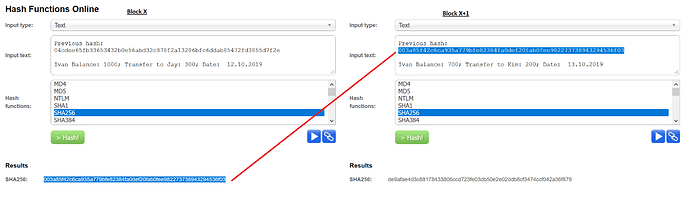
Just need a quick explanation for my business-minded friends, can I explain to them in the picture as shown? The output of SHA256 serves as the inputted Hash for the next block. As a result, it is impossible to change the “blockchain” as there is a need for the right previous output in order to proceed with the next block with any transaction information.
Thanks and hope to hear from you.
correct, each block has the hash of the previous block. so if you alter an older block in the blockchain, all the next blocks become invalid.
I’m not into programming in blockchain yet. But do understand given the consensus network all hashes and thereby transactions on the blockchain are final as if written in stone. That is one of the reasons the network is so secure.
Regarding Dapps. Can a Dapp built on etherium control another blockchain like BTC? If not then only controls the blockchain it was built on? That would give it a lot of limitations I would think. Also am I right in saying the only way to trigger a Dapp is by entering some kind of info on a site with a URL?
Hashing is kind of like a tumb print unique and cannot be reversed back to original content.There are many types of hashing algorithms.It’s the cryptography and sending of information between two parties that I am confused.
If you build a dapp on Ethereum, it stays within the limits of Ethereum. but you can program a dapp that uses ethereum and other blockchains as well. for example, you can program a game that uses Satoshi’s with the lightning network on bitcoin. and build in game assets using Ethereum. Using metamask you can trigger events (callbacks–like stuff) written in smart contracts on Ethereum.
i have a question about public and private keys.
If public key is derived from private key, and Ivan said its not possible to go the opposite way- from public key to private key. Then how are the public keys created, is it thru math? If yes, then theoretically it is possible to uncrack that key. And if its not derived thru math, then thru what? Because if its created randomly, then how the blockchain recognized the key? It has to be stored somewhere, as a key to unlock the door, but where is that stored and can that thing/place be hacked ?
Adresses are derived from public keys wich are created using your private key(random number). You can’t calculate private key from a public key. it uses an algorithm and hashes. (so It uses math and cryptography) You can sign transactions using your private key without reveiling it. so You can use your private key in a bitcoin wallet to proof that you are an owner of that batch of Bitcoins. Every Batch of bitcoins have a locking script on it. only the person who has the secret private key can unlock that batch to spend it.
You should watch this amazing presentation, This explains in detail How Keys and addresses work in Bitcoin. If you still have questions, feel free to ask.
hello
Thanks for the answer, i will watch the video!
without watching it, i still have the question how can i be sure that private key cannot be derived from public key?
Because so far its only said that you cannot do that, but thats what they thought about the MD5 aswell, and just saying that you cant do that
Is explaining very little.
But perhaps these questions resolve after i watch the video.
Thanks!
It uses ecliptic curve cryptography. It’s quite complex. Maybe in the distant future, quantum computers can break this. But by this time, Bitcoin could change this into a more secure way.