Hi Eric,
Sorry to hear you’ve been having problems with Remix 
You should be able to just right click on a file and select delete to delete it. You can also rename a file that way too.
You can create a new file by clicking on the icon on the left of the row of icons at the the top of the list of files. To make sure you’re in the right folder you can click on the folder you want the new file to be created in, before you create it.
The files you create in Remix are stored in a local cache folder. This means that if you clear your browser data and local cache you can lose your files. So, it’s always good to make a backup copy of your files somewhere else. This can be as simple as copying and pasting a file’s code into your text editor (Atom for example) and then saving it as a .sol file wherever is most convenient for you.
Some other students have had problems with Remix, so it’s not just you. If you’re using Brave then that might be the issue. I’m not sure of the exact problem, because I don’t use Brave myself, but it’s something to do with the Shields settings. Try using Chrome or Firefox, if you’re not already. Remix normally works much better for students on either of those browsers if they’ve had problems with others such as Safari or Opera. I use Remix in Chrome and it works absolutely fine for me.
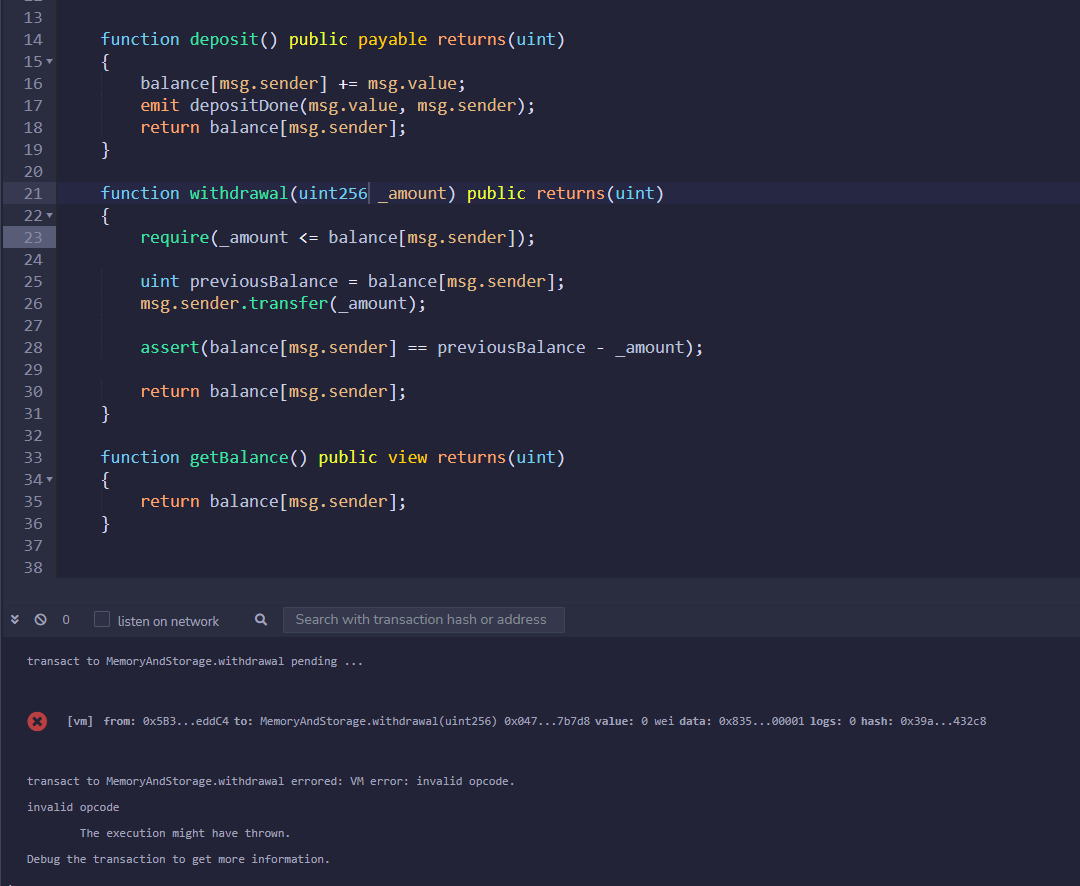
It seems to me from some of the code you’ve posted that you haven’t been compiling your files effectively. I would make sure you’ve got your Auto compile box checked in your Compiler Settings on the Solidity Compiler panel. This will compile your code as you go, and will immediately highlight any errors in red, and warnings in yellow/orange. Often just seeing that a line has an error or warning is enough to prompt you to check for any errors and correct them yourself. When you can’t see what the problem is, then you can read the actual error or warning message by either hovering over the red or yellow/orange indicator, or by navigating to the bottom of the Solidity Compiler panel.
I have no knowledge of any books, but here is a link to a playlist from the YouTube channel Eat The Blocks. I’ve seen some of this guy’s videos myself and I think they are particularly helpful for learning Solidity. The videos are quite short and the explanations clearly explained and well demonstrated with clear examples. You’ll find that several of the videos in this playlist correspond to specific sections of this course.
https://www.youtube.com/playlist?list=PLbbtODcOYIoE0D6fschNU4rqtGFRpk3ea
Also, it’s well worth spending your time browsing and reading other posts in these forum discussion topics, which include other students’ attempts and solutions, and the help, comments and feedback posted as replies. This is a valuable resource because it relates directly to the course material. You can use it not only to get help with the assignments, but also after finishing a section or particular assignment as a way to review what you’ve learnt, and to discover alternative coding solutions, and additional information.
Have you not seen the model assignment solutions that are provided? There should be links to them from the relevant lessons. Here is a link to the solution for this assignment:
https://github.com/filipmartinsson/solidity-0.7.5/blob/main/transfer-assignment-solution.sol
You can now read through my comments again, using the withdraw() function in this solution code as a reference.
You’ll find all the other solutions within the same repository. But remember, there are always alternative solutions, and so that’s why it’s also good to have a good look at some of what’s been posted here in the forum.
Anyway, I hope that gives you some ideas about how to tackle some of these difficulties 


 After you’ve done the assignment yourself, it’s really good to look at some of the other students’ solutions posted here in the forum, and the comments and feedback they’ve received: that way, you can check your solution and any points you were unsure about, and often learn some extra things.
After you’ve done the assignment yourself, it’s really good to look at some of the other students’ solutions posted here in the forum, and the comments and feedback they’ve received: that way, you can check your solution and any points you were unsure about, and often learn some extra things.