Hey Ernest,
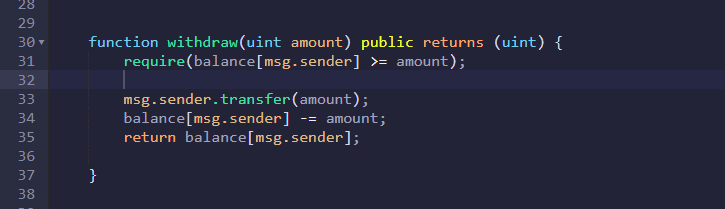
The require statement you’ve added is correct, 
You are also right that returns(uint) can be removed from the function header. It isn’t mandatory to include, and the function can still operate effectively without returning a value.
But you are missing one very important line of code…
If you deploy your contract, make a deposit, and then call your withdraw function (without the additional assert statement), you will notice that the caller’s address receives the requested withdrawal amount, but their balance in the mapping is not reduced (call getBalance to check this). I’m sure you can see that this is a very serious bug because, even though there is a limit on each separate withdrawal, this limit is never reduced to reflect each withdrawal.
msg.sender.transfer(amount) transfers ether from the contract address balance to the caller’s external wallet address, but it doesn’t adjust the individual user balances in the mapping. These balances perform an internal accounting role, and record each user’s share of the contract’s total ether balance. So, just as we increase a user’s individual balance when they deposit ether in the contract, we need to do the opposite whenever they make a withdrawal.
Your assert statement is incorrect and so it’s always failing whenever require evaluates to true i.e. when the amount requested for withdrawal is less than or equal to the user’s original balance (not their actual balance after having already withdrawn some ether because, as I’ve mentioned above, this isn’t being reduced). Maybe this is why your require statement isn’t failing and generating the error message you expect. However, even with your current incorrect assert statement, require should still trigger revert first whenever the amount requested for withdrawal is greater than the user’s original balance.
Until you add the additional line of code to adjust the user’s individual balance in the mapping, your assert statement is actually meaningless, because balance[msg.sender] is the same before and after the withdrawal. But even when you have added the additional line code, your assert statement will still be incorrect. By using an assignment operator the assert statement is changing the balance in the mapping as well as checking it. It must only check it. You also need to think carefully about which operand (which side of the comparison operator) to add or subtract the withdrawal amount from.
Once you’ve had a go at making the above modifications, have a look at this post which explains the importance of the order of the statements within your withdraw function body.
Let me know if you have any questions about how to correct this, or if there is anything that you don’t understand