1 Gaining influence over the network by creating multiple fake accounts.
2 Anonymity of nodes and/or using them under different identities.
- What is the general idea of a sybil attack?
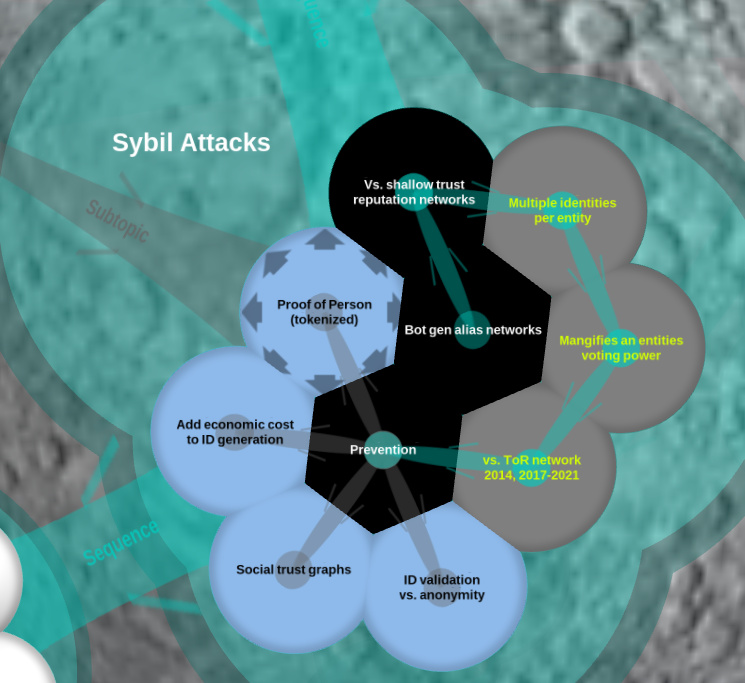
General idea of sybil attack is to create as many identities as possible per one entity (multiply identities) and they are used in peer-to-peer network. - What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
Identities can be produce very cheap, lack of verification, anonymity of addresses.
- to gain more (unjust) control over subject of an attack via 1 person faking many false identities
- too simple identity creation policy without reliable checking, which is hard to do anyway, especially if anonymity would like to be preserved
- What is the general idea of a sybil attack?
In short, it is trying to overwhelm a network with multiple identities that all map to the same entity which has access to the network. This can overwhelm the network and give the malicious actor control. - What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
Lack of compensating controls such as Indentity Validation, and, in the case of cryto networks, increased economic costs such as proof of work, which forces participants to spend money to be on the network.
- What is the general idea of a sybil attack?
An entity uses many identities to get bigger influence and control over a network. - What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
If it is easy and cheap to create multiple identities. No verification (or bad quality of verification) of the relationship between entities and identities.
- What is the general idea of a sybil attack?
A Sybil attack is an attack on a computer network service in which an attacker subverts the service’s reputation system by creating a large number of pseudonymous identities and uses them to gain a disproportionately large influence.
- What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
If you have a network which utilizes a voting system, the more identities you have, the more voting power and influence you have. The attacker can use this to their advantage.
Answer these questions:
-
What is the general idea of a sybil attack?
Sybil attack is when an entity creates multiple identities to disrupt or gain influence to a peer to peer network. -
What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
Easy to create multiple identities.
1:
Sybil attack is a type of attack on a computer service in which an attacker subverts the service’s reputation system by creating a large number of pseudonymous identities and using them to gain a disproportionately large influence.
2:
You can easily create new identities
1. What is the general idea of a sybil attack?
“The Sybil attack is an attack wherein a reputation system is subverted by creating multiple identities”
In theory one’s node could connect to malicious peers only, and therefore be fed a “false truth” on what is the longest chain.
2. What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
Going by the article the 2 that would apply are :
-
Identity validation : Commonly used to “prevent” Sybil attacks, however not truly applicable to pseudonymous networks.
-
Personhood Validation
Worthy to consider in the case of BTC there is also an economic cost to attempt a Sybil Attack in the form of running and maintaining nodes. And the attacked node could always connect to an honest peer at any time. Making the longevity of such potential attacks short.
- What is the general idea of a sybil attack?
- A Sybil attack is a type of attack on a computer in which an attacker subverts the service’s reputation system by creating a large number of pseudonymous identities and using them to gain a disproportionately large influence.
- What deficiencies within a system (such as a cryptocurrency network) can allow a Sybil attack to occur?
- Deficiencies and vulnerabilities within a system allow a Sybil attack to occur when a single malicious entity produces many copies of its pseudonymous and therefore imposes its will or demands without revealing that it only comes from a single source. In cryptocurrency, this kind of attack can be countered by way of Proof of Work (PoW) or Proof of Stake (PoS) to increase the economic cost of such activity.
- Is the ability of a single entity to create different identities to affect how the network works
- Anyone can anonymously create multiple identities, generally for free
-
The creation of many false identities in an attempt to gain control of the network.
-
poor consensus mechanism
-
What is the general idea of a sybil attack?
The general idea of a sybil attack is to flood the entire network with as much fictitious identities as possible. Thereby creating turmoil and giving the bad actor control or influence over a vulnerable network. -
What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
The deficiencies that would probably allow a sybil attack to take place on a cryptocurrency network would probably be the anonymity along with the decentralization of the network.
-
What is the general idea of a sybil attack?
using fake identities to influence a network like using a bunch of bots for one specific purpose like subscribing to someone or liking someones video -
What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
when you can easily create more than one identity because everything is done anonymously
-
One entity controlling or impersonating as multiple entities on a peer to peer network. the controlled entities can propagate false information to them pretending to be many.
-
Having a node that has all close by nodes that it connects to be the same entity. It is also easy to create new entities. (Nodes + addresses)
- What is the general idea of a sybil attack?
- Attackers will create multiple identities in order to take over the network by acquiring disproportionate level of control such as voting power.
- What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
- Creating a new wallet on cryptocurrency network is easy and does not require proof of personhood.
1.creation of fake accounts that may lead to misinformation or manipulation
2. Anonymity and the entry cost to participate in the activities of blockchain industry as a user is very low and easy.
What is the general idea of a sybil attack?
A type of network attack in which an attacker creates a large number of accounts to gain a disproportionately large influence over a system.
What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
Permissionless access coupled with absence of KYC makes sybil attacks easy to pull off in crypto. Sybil attacking of airdrops is particularly rife.
1. What is the general idea of a sybil attack?
- It is the process of surrounding a node with multiple nodes in order to block off their connection with the blockchain and think that they are connected but the multiple nodes controlled by the attacker can limit the information that single node receives and can easily make a transaction and run off.
2. What deficiencies within a system (such as a cryptocurrency network) can allow a sybil attack to occur?
- New nodes can be created by a single person