RIP SafeMath 
Thanks for sharing! Nice teamwork
Indeed, v0.8 of solidity kills SafeMath 
Carlos Z.
@Ivan Maaate if you didn’t say anything about the pimple I wouldn’t have paused the video, get back and have a look 

Ivan is a Legend 
Thats a fact! haha 
It is what happens when you drink coffee black everyday, no milk, no sugar.
As Always
Stuff like this is such a treat 
Also his joy at seeing the _receivers balance after doing the batchSend without the fix is like telling a kid a naughty knock knock joke for the first time.
Small things like this make him such a good teacher because it feels he’s authentically engaged in what he’s teaching.
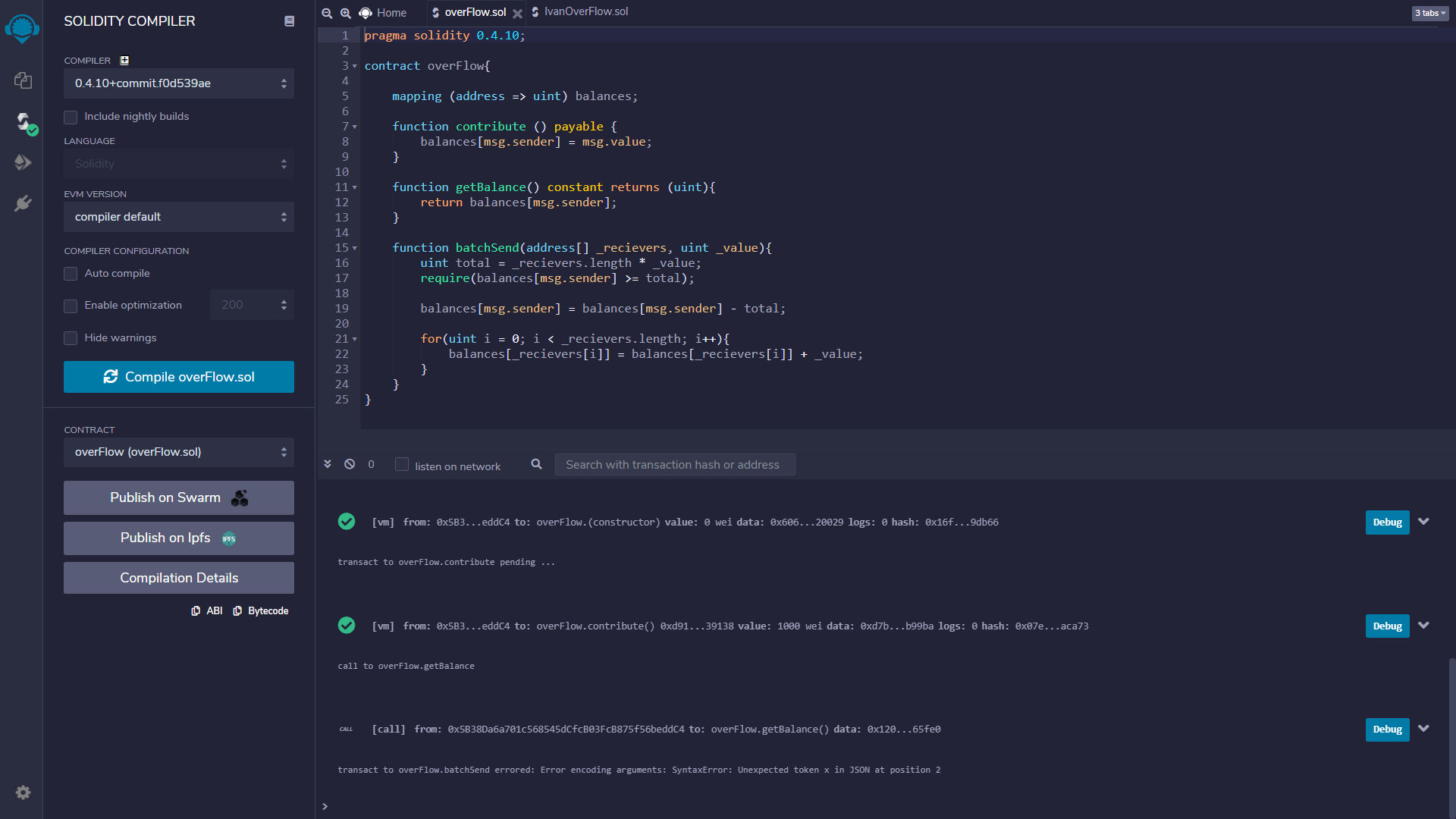
I am also getting an error and cant seem to figure what’s the cause. Here is my code and error:
pragma solidity 0.4.10;
contract overFlow{
mapping (address => uint) balances;
function contribute () payable {
balances[msg.sender] = msg.value;
}
function getBalance() constant returns (uint){
return balances[msg.sender];
}
function batchSend(address[] _recievers, uint _value){
uint total = _recievers.length * _value;
require(balances[msg.sender] >= total);
balances[msg.sender] = balances[msg.sender] - total;
for(uint i = 0; i < _recievers.length; i++){
balances[_recievers[i]] = balances[_recievers[i]] + _value;
}
}
}
transact to overFlow.batchSend errored: Error encoding arguments: SyntaxError: Unexpected token x in JSON at position 2
Also nothing has been transfered and I did set the compiler to 4.10+commit
Also just to clarify, so if we are using compiler version higher than 0.8.0 we don’t really need to use SafeMath? this lesson basically is for our awareness and for those who are using older versions of the compiler?
Indeed, you can check it here https://docs.soliditylang.org/en/latest/080-breaking-changes.html#how-to-update-your-code
The idea of the lesson is to made you aware of how underflow/overflow works , the error you provided does not said too much, would be great if you can provide an screenshot about it (but might be that is mean to fail).
Carlos Z
thanks for the reply, here is my printscreen
I have tested your contract in the following way, and it works (has expected it will create tokens from the overflow)
pragma solidity 0.4.10;
// ["0xAb8483F64d9C6d1EcF9b849Ae677dD3315835cb2", "0xCA35b7d915458EF540aDe6068dFe2F44E8fa733c", "0x4B20993Bc481177ec7E8f571ceCaE8A9e22C02db"]
contract overFlow{
mapping (address => uint) balances;
function contribute() payable{
balances[msg.sender] = msg.value;
}
function getBalance() constant returns(uint){
return balances[msg.sender];
}
function batchSend(address[] _receivers, uint _value){
uint total = _receivers.length * _value;
require(balances[msg.sender] >= total);
balances[msg.sender] = balances[msg.sender] - total;
for(uint i = 0; i < _receivers.length; i++){
balances[_receivers[i]] = balances[_receivers[i]] + _value;
}
}
}
Your screenshot does not show how are you sending the address array to the function, or if you deployed it.
Carlos Z
ok i tried it again and it did work this time for me too, not sure why didn’t work before. so it did overflow this time as I wanted to, cool many thanks for help. I think I wasn’t putting " signs the last time but i remember that i did originally when was testing it so not sure. anyway it does work now.
Is it still necessary to use SafeMath in today’s (August 2021) version of Solidity? I remember reading somewhere that Solidity now automatically checks for over- and underflow.
Yes, since solidity v0.8.0 its optional to use SafeMath, because this methods are now inherited into solidity, https://docs.soliditylang.org/en/v0.8.0/080-breaking-changes.html
Carlos Z
Hyperinflation Reading Assignment Questions
- By an automized system that checks for suspicious transactions (transferring unreasonably large tokens)
- BatchOverflow
- batchTransfer
- Because the same code was used
- Because you can’t fix the code. Once it’s on the blockchain, it’s irreversible.
- OkeX shut down all trading, but other exchanges had to respond either.
In the solution to the hyperinflation or overflow bug, did we really need safemath at the end? Could we not use the same assert function in our original code?
Something like assert that the number does not exceed a certain number of zeros so it does not overflow or underflow?
I am pretty sure you could do that but it would be more infeasible as you would need to remember to put in the customized assert function each time you run anything that has risk of over/underflow
Hi everyone,
I have a question. On the video, Ivan said that the uint in total variable can hold until 256 bits. How does the function knows how many digits can allow ? Why overflow occurs without knowing the digit limit ?
I have some problem with this code. it said "from solidity:
ParserError: Expected ‘{’ but got ‘public’
–> ETH SC Security/Overflow.sol:13:42:
|
13 | function getBalance() returns (uint) public {
| ^^^^^^"
Below is my code:
pragma solidity ^0.8.16;
//SPDX-License-Identifier: UNLICENSED
contract Overflow {
mapping (address => uint) balance;
function contribute() payable public {
// 1 wei = 1 token
balance[msg.sender] = msg.value; //if 1 wei = 100 token, balance[msg.sender] = 100 * msg.value
}
function getBalance() returns (uint) public {
return balance[msg.sender];
}
}
Where should I put “public”? If I don’t put “public” like in the video, it said
“from solidity:
SyntaxError: No visibility specified. Did you intend to add “public”?
–> ETH SC Security/Overflow.sol:13:5:
|
13 | function getBalance() returns (uint) {
| ^ (Relevant source part starts here and spans across multiple lines).”
returns is always the last option on the function header.
function getBalance() public returns (uint) {
return balance[msg.sender];
}
Carlos Z
