-
What information does PrivateSend conceal, and by what method?
The ownership of the coins by using the CoinJoin method. -
How do masternodes improve on the initial CoinJoin proposal?
It makes it more easier (from a user’s point of view) to make use of the CoinJoin transaction. Because the masternode takes care of gathering the different transaction inputs and joining them together. -
Alice send some DASH to Bob using PrivateSend. Describe how an attacker could link their addresses.
If the attacker hacks the masternode, he/she can read transaction data. Also, the attacker could run a masternode to sniff the PrivateSend transactions. -
In what way could PrivateSend be more risky than a normal Bitcoin Transaction?
In PrivateSend (like in bitlaundry) we have a “middle man” (or central authority) that has all the transaction information. If this centralized authority gets hacked (or supplanted), we lose our privacy.
- The ownership trail is concealed. Except in front of the masternodes.
- A masternode collects the coins from different users, mixes them together in the CoinJoin Transaction
- If the masternode processing the coinjoin is a spy
- The fact of using it makes you suspicious.
- PrivateSend uses the method of Coinjoin. It conceal the information which coins (how many) were send from one address to an other (because the coins are mixed).
- Dash’s masternode system construct the CoinJoin transaction. Dash users that wish to mix their coins contact a random masternode, which then collects the coins from the different users, and mashes them together in the CoinJoin transaction. It’s important to note that the masternode cannot steal the coins.
- We could spay or attack the masternodes. Or the owner of the masternote could do some shady things.
- You as a sender have the option to decide if you like to mixing your trx. Because we use the step of mixing we are suspicious of hiding something and therefor we could be moved in focus of some goverment spay.
1. What information does PrivateSend conceal, and by what method?
The identity of the sender and the reciver by “mixing up” the coins in a three way transaction that is made by a masternode.
2. How do masternodes improve on the initial CoinJoin proposal?
It makes it easier for people to use. When the masternode is the one constructing the transaction.
3. Alice send some DASH to Bob using PrivateSend. Describe how an attacker could link their addresses.
If an attacker has control over the master node or gets information from it. They can see the “switch up” of the coins that is happening in the transaction and just follow the link from there.
4. In what way could PrivateSend be more risky than a normal Bitcoin Transaction?
If the master node is corrupt and people can see that you have used PrivatSend which shows that you might have something to hide,
to learn about DASH feature you should search and read the specs from the own DASH source 1st,
https://docs.dash.org/en/stable/introduction/features.html#privatesend
https://dashpay.atlassian.net/wiki/spaces/DOC/pages/1146924/PrivateSend
then you can see what other critics (Bitcoiners maxims do not like much DASH, so instead rose-color-glasses they tend to see most things through shit-glasses all other projects)
So read both sides and judge for yourself.
- PrivateSend changes coins addresses into clean decimal values/nominations (1, 0.1, 0.01, 0.001, and so on) by ‘coinjoining’ coins (from several input address), and by several mixing rounds, from other network wallets/users participants selecting ‘randomly’ from a random set of masternodes that are providing this mixing service. The coinmixing transactions will generate hundreds of newly addresses with small subunit of DASH ready to be used to compose any amount needed.
- The user does not depend so much on the other user parties to get coins re-denominated and in fresh addresses, it does depend that other users exist wanting to request the PrivateSend coinmixing service.
- It is a 2 step, Alice needs to get ‘clean’ coins re-denominated 1st, she can do this step in anytime like anyone goes to get cash change coins just to have it ready in your wallet.
Then 2nd step Alice only when she needs to send Bob some DASH, can be anytime not related to the 1st step time. Alice either selects from the ‘private-send’ available coins, or just click in the wallet that she wants to ‘private-sent’ and the wallet selects from the clean coins available (each coin received from the coinmixer tx’s, never used before) and send Bob the amount she needs to send. An attacker can only figure out anything about Bob if Bob does not use a newly created address. The attacker can not find anything about Alice unless he have access to Alice wallet and if the wallet it is un-encrypted without a password. - I can only think about a technical risk (unknown bug that would lead to lost of coins) because the two step process of PrivateSend is more complex and total different than a normal Bitcoin Transaction, so please don’t compare “simple normal apples to orange juice in a crystal glass with a straw” …
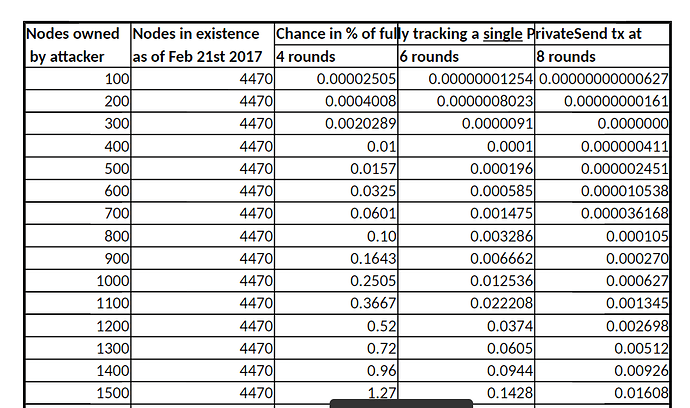
Risk Analysis of several random Masternodes being spy and amount of mixing rounds
https://dashpay.atlassian.net/wiki/spaces/DOC/pages/1146924/PrivateSend?preview=/1146924/104866022/Probabilities_PrivaTx.xlsx
-
What information does PrivateSend conceal, and by what method?
Hides the connection between sender and receiver -
How do masternodes improve on the initial CoinJoin proposal?
The masternode mix input transactions together and send them to new generated addresses, this can be repeated 8 times. -
Alice send some DASH to Bob using PrivateSend. Describe how an attacker could link their addresses.
By spying the nodes and checking the addresses and could find out the addresses of a sender and receivers and link them together. -
In what way could PrivateSend be more risky than a normal Bitcoin Transaction?
When you use PrivateSend it’s already suspicious, further you have to trust the masternode.
- Private send hides the connection between sender and receiver by mixing up coins in a 3 way tx made by the masternodes
- it does not require someone to construct of TX, masternodes do it. It´s more user friendly (GUI).
- He could link their addresses if he has control/influences over the master node.
- If you use private send you are already suspicious. You gotta hope that masternodes is not influenced/corrupted.
It’s a fair point!
Thanks for the detailed response 
- What information does PrivateSend conceal, and by what method?
PrivateSend is an implementation of CoinJoin. It mixes transactions in an attempt to break the association between owners and accounts.
- How do masternodes improve on the initial CoinJoin proposal?
Anonymity of participants- master nodes match up the mixing parties for you. Mainly seems like a UX/convenience upgrade. I don’t like the 3rd party hackable masternodes.
- Alice send some DASH to Bob using PrivateSend. Describe how an attacker could link their addresses.
The addresses could be linked by accessing the PrivateSend database.
- In what way could PrivateSend be more risky than a normal Bitcoin Transaction?
If breached, masternodes could reveal connections between addresses and the fact that you have a reason to pursue privacy.
1. What information does PrivateSend conceal, and by what method?
PrivateSend conceals the link between sender and recipient by the method of mashing coins together (between three users up to eight times).
2. How do masternodes improve on the initial CoinJoin proposal?
Masternodes improve the initial CoinJoin proposal by removing the step of users creating the coin-mixing transaction themselves.
3. Alice send some DASH to Bob using PrivateSend. Describe how an attacker could link their addresses.
An attacker could link Alice and Bob’s addresses by compromising the virtual private servers upon which many masternodes operate therefrom.
4. In what way could PrivateSend be more risky than a normal Bitcoin Transaction?
PrivateSend could be more risky than a normal Bitcoin transaction through the possible reveal that your now-visible transaction was preferred to be private, which is in a way outing yourself out.
1. What information does PrivateSend conceal, and by what method?
PrivateSend uses CoinJoin to obfuscate the link between sender and receiver in a transaction. The join is facilitated by Master Nodes.
2. How do masternodes improve on the initial CoinJoin proposal?
Users can opt to mix their coins multiple times through different Master nodes.
3. Alice sends some DASH to Bob using PrivateSend. Describe how an attacker could link their addresses.
DASH’s CoinJoin only combines transactions from 3 users, this means the anonymity set is rather small. If the transaction amounts are not uniform this would make it even easier to figure out which amount came from where.
Second, the Master Nodes have full knowledge of what coins went where. If a bad actor operates a Master Node, or compromises one they could gain accesses to that information.
4. In what way could PrivateSend be more risky than a normal Bitcoin Transaction?
Using PrivateSend is optional and costs more, so most users probably don’t bother. This leads to the stigma that only people with “something to hide” use PrivateSend. The links between sender and receiver are obfuscated, but the fact that PrivateSend was used is publicly visible in the blockchain. This makes using PrivateSend more risky.
It basically moves the user’s balance to a fresh address, mixing the UTXOs with other users. The method is called CoinJoin and was proposed for bitcoin first.
The masternodes make it easy to for the user to find other participants who also want to do a coinJoin (private send).
By hacking, bribing or coercing (governments) a masternode. The executing masternode knows who participate in the CoinJoin.
It migth look suspicious if a user used PrivateSend since it is an optional feature of DASH.
-
It uses an implementation of CoinJoin to group transactions and obscure the source/destination of transactions.
-
Masternodes work in such a way that the grouped transactions are “re-grouped” by 3 different masternodes, further stirring up input sources and remixing several times.
-
Having access to a Masternode would allow the details to be revealed. An attacker could run a masternode (or even all three in a set) and record the details of the transactions.
-
Even if privacy is achieved, the fact that the coins were mixed are not. This can raise suspicion about why someone seems to think they need to mix their coins.
1- by using CoinJoin, Privatesend mix coins from three senders creating new addresses to scramble the coins and send it back to the owners.
2-Masternodes Construct these CoinJoin transactions.
3- Masternodes in private server are vulnerable to spies, and they have the info of origin and destiny of the coins mixed by Private send.
4- Masternodes could also be run by governments and agencies.
- What information does PrivateSend conceal, and by what method?
- PrivateSend conceal the link between two transactions, making it possible to “clean” bitcoin. PrivateSend is an implementation of CoinJoin.
- How do masternodes improve on the initial CoinJoin proposal?
- MasterNodes join several transactions, just like a normal CoinJoin, but MasterNodes can’t steal your coins.
- Alice sends some DASH to Bob using PrivateSend. Describe how an attacker could link their addresses.
- MasterNodes themselves can link this information together
- You have to trust the MasterNode operator. It could be run a malicious actor.
- coins ownership by the CoinJoin principle;
- Nodes collect the coins and distribute them automatically via the masternodes which cannot steal the coins
- Easily bu running a masternode himself. In this way he knows both sender and receiver addresses
- Nobody really knows who runs these masternodes. This means that they could be run by Governmental Agencies. It is not a trustless setup in simpler terms.
-
What information does PrivateSend conceal, and by what method?
PrivateSend hides the details of a transaction by using CoinJoin. Afterwards it’s not possible to see, who the owner was and who the receiver is. -
How do masternodes improve on the initial CoinJoin proposal?
If a user want to have a transaction with more privacy, he select CoinJoin and a random masternode will collect his and two other transactions and mixed them up in a CoinJoin transaction. This can happen up to 8 times: Another masternode will collect the mixed transaction and mixed it again and so on…After finally the first 3 transactions will arrive at their final destination. -
Alice send some DASH to Bob using PrivateSend. Describe how an attacker could link their addresses.
The attacker could hack the first masternode, cause this masternode knows who the owner of the DASH was and to whom this DASH are going. -
In what way could PrivateSend be more risky than a normal Bitcoin Transaction? A lot of DASH was mined in the first week (25%). Than means, that the first masternodes could already collect a lot of DASHs, so theoretically it’s possible for just a few masternodes to controll the CoinJoin transaction and spy on some of the users and sell the information (or worse), if needed.
- What information does PrivateSend conceal, and by what method?
- Hide the private info of Sender and receiver by CoinJoin
- How do masternodes improve on the initial CoinJoin proposal?
- It helps to construct the CoinJoin TX.
- Alice send some DASH to Bob using PrivateSend. Describe how an attacker could link their addresses.
- Run the masternotes and reveal the addresses
- In what way could PrivateSend be more risky than a normal Bitcoin Transaction?
- When Spy operating masternodes and not many users are using PrivateSend
- PrivateSend conceals the linkage between wallet addresses and the user.
- Masternodes improve on the initial coinjoin proposal by putting the trust of mixing to the blockchain. Masternodes cannot steal the coins being mixed.
- If the security of the masternode operation is compromised the attacker would have access to all transaction linkages to all users.
- PrivateSend could be considered more risky because you cannot hide the fact that your coins went to a mixing service. This can be frowned upon and even get some of your wallet addresses banned or flagged for using a mixing service.
- Coinjoin; it conceals to whom coins are sent by disrupting the trail of ownership.
- More user friendly (easy to select from drop down menu). The Masternode will then construct the coinjoin
- The attacker could either be the Masternode or gain access to the information of the Masternode, from where it is easy to discover from whom to whom the coins were sent.
- By using PS it is quite visible that the user wanted to have privacy, which could actually attract the attention, bc all other users won’t be using that feature as they would care less about privacy.