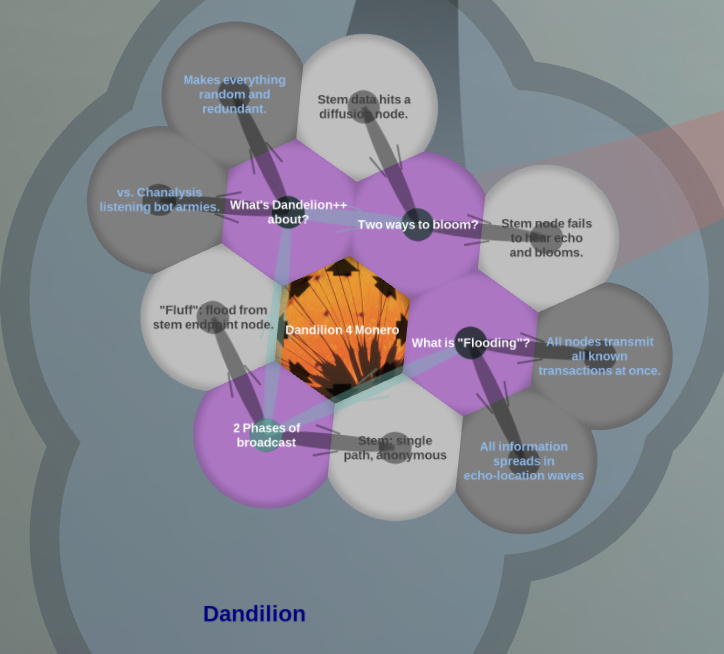
- It is a process, executed by a Monero node, which initiates the broadcast of a new transaction.
- Stem or Anonymity phase --> It is a process for finding a proxy node to broadcast
Spreading or Fluff phase --> It is the process that broadcast transactions to all nodes on the network.
These two phases use different sets of peer connections with the important difference that the anonymity phase connection set changes with time. - Dandelion ++ aims to solve the problem of nodes that try to undermine user anonymization by breaking the rules.
- Either using the epochs method or using the fail-safe mechanism.
• Flooding occurs when a Monero nodes starts a transaction and communicates it to all its peers, which at the same time do the same process, it I described as a waive, there are some checks involved to prevent redundant communication.
• 1st called Anonymity (or stem) phase, which is to find a node to broadcast, and, 2nd spreading or (fluff) which is another process for broadcasting. The 2 phases use different sets of peer connections with the important differences that anonymity set changes with time.
• Dandelion++ aims to resist a large scale, rule braking, deanonymization attack. Something that Dadelion would not be able to if there was some node not playing by the rules.
• 1st ; if a node is a diffuser whenever its given a Tx to relay as a stem phase, it instead broadcasts it using diffusion, thereby starting the fluff phase. 2nd ; this is a complementary piece of Dandelion++ called the fail-safe mechanisms , if a timing threshold passes by and a node does not receive the same transaction back during stem phase, it would start its own fluff phase.
-
What is ‘flooding’?
The communication proces to broadcast transactions to all the peers it’s connected with and those peers connect to others, itś like a big wave through all the peers in connection with each others. Think of the seeds of dandelion flower, when you blow the seeds away they go every where, some will grow a new flower, some will fall death. -
What are the two phases of a Dandelion broadcast and what happens in each phase?
It will seek first a proxy node along a special linear search path, then it will broadcast information almost spontaneously rapidly and symmetrically. -
What potential weakness of Dandelion does Dandelion++ aim to address?
There could be still a lot of non-honest nodes which still monitor transactions and make conclusions where a transaction could come from. -
Under the Dandelion++ protocol, what are the two ways to transition from the ‘stem’ phase to the ‘fluff’ phase?
The epoch switch method and the fail safe mechanism.
- “Flooding” is a propagation technique to broadcast new transaction
- first step is the anonymity (or stem) phase to define a process for finding a new proxy node to broadcast, the second step is the spreading (or fluff) phase to establish another process for broadcast
- the large-scale rule-breaking deanonymization attacks
- epoch and fail-safe mechanism
-
Flooding is a way of routing data whereby each packet of data is sent out on all outgoing lines except the line on which it arrived.
-
The two phases of a Dandelion broadcast are the anonymity (or stem) phase and the spreading (or fluff) phase. In the anonymity phase a proxy node is sought along a special linear path. In the spreading phase, once the proxy node is determined, the information is spread rapidly in many directions.
-
The potential weakness of Dandelion which Dandelion++ seeks to address is the possibility that a node may not follow the rules of the network, or remain as a passive observer. Dandelion was only spy-resistant when all the nodes participated in the process, and did so honestly.
-
Under the Dandelion++ protocol the two ways to transition from the “stem” phase to the “fluff” phase are; a) using the Epoch system, whereby the broadcast travels along the network in intervals, and at each interval the node it reaches can randomly diffuse the transaction, thereby starting the “fluff” phase - or it can just relay the transaction. And b) the fail-safe mechanism, where each node which relays a transaction during the “stem” phase starts a timer. If the timer deadline passes without the transaction coming back, the node starts its own “fluff” phase.
- What is ‘flooding’?
It is a p2p process where the transaction is broadcast to all its peers with some checks to prevent redundant communication.
- What are the two phases of a Dandelion broadcast and what happens in each phase?
=> Stem: This is the phase for seeking a proxy node to hide the IP address.
=> Fluff: The spreading phase to spread the information rapidly and symmetrically.
- What potential weakness of Dandelion does Dandelion++ aim to address?
Dandelion++ aim to address the potential weakness could that be a large-scale rule-breaking deanonymization attacks.
- Under the Dandelion++ protocol, what are the two ways to transition from the ‘stem’ phase to the ‘fluff’ phase?
The epoch switch method or through the fail safe mechanism.
- When a node communicates a transaction to all its peers, who in turn communicate to all their peers, and so forth, with some checks to prevent redundant communication, the information travels in all directions over the network like a wave; this is called flooding.
- Dandelion defines a process for finding a proxy node to broadcast, called the anonymity (stem) phase. And it establishes another process for broadcast, called the spreading (fluff) phase. During the stem phase proxy node is sought out along a special linear search path, then from this proxy node spreading the information rapidly and symmetrically (fluff).
- Dandelion++ covers problems arising from large scale rule-breaking attacks from both friendly and unfriendly nodes to deanonymize.
- Epoch switch and fail safe.
1. What is ‘flooding’?
A Monero node starting the broadcast of a new transaction uses a process called flooding. It communicates the transaction to all its peers, who in turn communicate to all their peers, and so forth, with some checks to prevent redundant communication. The information travels in all directions over the network like a wave. Some cryptocurrencies, like Bitcoin, randomize the timing of this broadcast, but Monero does not.
2. What are the two phases of a Dandelion broadcast and what happens in each phase?
Dandelion defines a process for finding a proxy node to broadcast, called the anonymity (or stem) phase. And it establishes another process for broadcast, called the spreading (or fluff) phase. In general, the two phases use different sets of peer connections with the important difference that the anonymity phase connection set changes with time.
3. What potential weakness of Dandelion does Dandelion++ aim to address?
Nodes that share the info that powers Monero are identified using Internet Protocol (IP) addresses, though, exposing risk that observers can connect IP addresses to transactions, deanonymizing the data they contain. Dandelion++ is a method for hiding this connection
4. Under the Dandelion++ protocol, what are the two ways to transition from the ‘stem’ phase to the ‘fluff’ phase?
For each epoch, a node classifies itself as either a relayer or a diffuser. The mode is determined at random at the start of the epoch. If a node is a diffuser, whenever it is given a transaction to relay as stem phase, it instead broadcasts it using diffusion, thereby starting the fluff phase.
There is an additional, complementary piece to Dandelion++ called the fail-safe mechanism. Each node that relays a transaction during stem phase starts a timer for that transaction. If a time threshold passes without the node receiving the same transaction back during a fluff phase, it starts its own fluff phase.
-
A Monero node starting the broadcast of a new transaction uses a process called flooding. It communicates the transaction to all its peers, who in turn communicate to all their peers, and so forth, with some checks to prevent redundant communication. The information travels in all directions over the network like a wave. Some cryptocurrencies, like Bitcoin, randomize the timing of this broadcast, but Monero does not.
-
The two phases of a Dandelion broadcast are the stem phase and the fluff phase.
Dandelion defines a process for finding a proxy node to broadcast, called the anonymity (or stem) phase. And it establishes another process for broadcast, called the spreading (or fluff) phase. In general, the two phases use different sets of peer connections with the important difference that the anonymity (stem) phase connection set changes with time. The descriptive name Dandelion comes from the process of first seeking out a proxy node along a special linear search path, then from this proxy node spreading the information rapidly and symmetrically—the shape of information flow resembles a dandelion. -
Dandelion++ tweaks Dandelion to resist large-scale rule-breaking deanonymization attacks.
-
Under the Dandelion++ protocol the two ways to transition from the stem phase to the fluff phase is either by using the “epochs switching” method or through the “fail-safe mechanism” (using a timer).
1.Flooding is the process of nodes broadcasting a transaction across the network to other nodes
2.There is a stem phase where a node a few steps away from the core node is selected to broadcast the transaction then the Fluff phase where the transaction is then broadcasted from.
3.There will be a small amount of delay created by the stem phase and another small bit in the diffusion stage. Also if there is a black hole attack (a node just swallows a transaction without dispersing it further) then the lack of acknowledgement and re transmit could take a few minutes.
4.There is the “fail safe mechanism” which belongs to the fluff phase where: Each node that relays a transaction during stem phase starts a timer for that transaction. If a time threshold passes without the node receiving the same transaction back during a fluff phase, it starts its own fluff phase. This serves two purposes: It frustrates attempts at deanonymization using timing, and it defeats so-called black-hole attacks where adversarial nodes discard transactions during the stem phase rather than relaying them.
And there is the second mechanism is the “Epochs Switching”
-
What is ‘flooding’?
A mass broadcast or wave of transaction information to all peers which is communicated to surrounding peers/nodes. -
What are the two phases of a Dandelion broadcast and what happens in each phase?
Dandelion starts by sending an initial update for transaction to an anonymity proxy node then begins the flood transmission -
What potential weakness of Dandelion does Dandelion++ aim to address?
The “stem” phase adds a delay to the transmission, and diffusion adds a random delay during “fluff”. The primary risk is that nodes may not be honest and undermine anonymity. -
Under the Dandelion++ protocol, what are the two ways to transition from the ‘stem’ phase to the ‘fluff’ phase?
The stem phase uses the dynamic connectivity to select random nodes for propagation picking two random relays as “epoch switching”. The second is a fail-safe when the node simply begins its own fluff process if the transaction does not return within a given time threshold.
- It is a broadcasting process used to communicate transactions across the network, by having all nodes communicating the information to their peers which will then do the same and so on, so forth.
- Dandelion defines a process for finding a proxy node to broadcast, called the anonymity (or stem) phase. And it establishes another process for broadcast, called the spreading (or fluff) phase.
- Dandelion++ tweaks Dandelion to resist large-scale rule-breaking deanonymization attacks.
- Either by using the “epochs switching” method or through the “fail-safe mechanism”.
- Flooding is when a new transaction is communicated to all its peers, who in turn communicate to all their peers, and so forth, with some checks to prevent redundant communication.
- Anonymity (or stem) phase and spreading (or fluff) phase.
- Dandelion++ tweaks Dandelion to resist large-scale rule-breaking deanonymization attacks.
- Epochs and fail safe mechanism.
!; Flooding is sending info / TRxs simultaneously to may nodes who in turn send it to many other nodes
2:Creating a stem ( Anonymity) which is sent to nodes who in turn spread it (Broadcast /Flood the network) each nodes deciding and swithing from stem to broadcast.
3: IP discovery by large sclae attacks and botnets in the network not following the rules
4:Using epoch or a system where nodes change from diffuser to receivers fluff to stem
What is ‘flooding’?
According to the article,it’s when a transaction is communicated to all the peers who then communicate to all there peers, continuing to “flood” the network.
What are the two phases of a Dandelion broadcast and what happens in each phase?
The 1st Phase is called the Stem/ Anonymity phase. The stem phase connection set changes with time,it seeks out a proxy node along a special linear search path, like the stem of a Dandelion.
The 2nd Phase is called spreading/ fluff phase, continuing from the second face, from the proxy node it spreads the information out rapidly and symmetrically. the information flow is supposed to resemble a dandelion.
What potential weakness of Dandelion does Dandelion++ aim to address?
The potential weakness the Dandelion ++ hopes to address is a malicious actor/ spy trying to gather any and every bit of information it can about transactions and users. Especially IP addresses.
Under the Dandelion++ protocol, what are the two ways to transition from the ‘stem’ phase to the ‘fluff’ phase?
The new stem phase, randomly chooses which path will it take, and how the nodes will respond, will it be a relay or a diffuser. even if the transaction isn’t picked up by the node, it will still bloom, thus faking a potentially transaction while the real one is still going through, waiting to be picked up.
- What is ‘flooding’?
flooding- happens when a nodethe transaction to all its peers, who in turn communicate to all their peers, and so forth, with some checks to prevent redundant communication. The information travels in all directions over the network like a wave.
- What are the two phases of a Dandelion broadcast and what happens in each phase?
Dandelion defines a process for finding a proxy node to broadcast, called the anonymity (or stem) phase. And it establishes another process for broadcast, called the spreading (or fluff) phase.
- What potential weakness of Dandelion does Dandelion++ aim to address?
Dandelion++ tweaks Dandelion to resist large-scale rule-breaking deanonymization attacks.
- Under the Dandelion++ protocol, what are the two ways to transition from the ‘stem’ phase to the ‘fluff’ phase?
the first way is this-The fluff phase in Dandelion++ uses diffusion, the flooding process where the timing of the communications are random to make it harder for spy nodes to locate the source
the second way called the fail-safe mechanism. Each node that relays a transaction during stem phase starts a timer for that transaction. If a time threshold passes without the node receiving the same transaction back during a fluff phase, it starts its own fluff phase.
- A way of communicating transactions through the network, sending it to all the nodes peers that sends it to all its peers and so on.
- First the transaction is sent to a proxy node (stem) which then symmetrically spreads it to other nodes (fluff).
- The adversary may not be honest and are seeking to link transactions to IP address.
- For each new epoch nodes classify themselves as either relayers (stem) diffussers (fluff). When a node sends a transaction in stem phase it waits for some time period to receive the transaction back in a fluff phase. If that does not happen, it starts its own fluff phase.
Monero node communicates the transactions to all its peers, who in turn communicate to all their peers, and so forth, with some checks to prevent redundant communication. The information travels in all directions over the network like a wave. Some cryptocurrencies, like Bitcoin, randomize the timing of this broadcast, but Monero does not.
- Stem phase (finding a proxy node to broadcast) – Fluff Phase (establishes another process for broadcasting)
- Dandelion++ tweaks Dandelion to resist large-scale rule-breaking deanonymization attacks.
a discreet intervals (timing of communication is random), called epochs.
b fail-safe mechanism (when transacction reaches a node diffuser, it gets diffused and processed
- Flooding is transaction broadcasting from sender’s node to all other connected peers with farther broadcasting to all their peers with some protection checks to prevent redundant communication.
- First phase or the anonymity (stem) phase is a process of finding a proxy node to broadcast transaction.
Second phase or the spreading (fluff) phase is when transaction broadcasted to the peers of the network. - Dandelion is good against passive adversary, but it does not protect from large scale rule-breaking deanonymization attacks. Dandelion++ will preserve IP anonymity even if botnet with spy nodes is distributed throughout the network.
- First way is when transaction is broadcasted to the node which is currently in a ‘fluff’ mode.
Second way is that node set a timer since transaction was broadcasted in a stem mode and in case if this node does not receive this transaction within some specific time period from other nodes, the node will broadcast this transaction in a fluff mode.